After you add the App Check library to your app, but before you enable App Check enforcement, you should make sure that doing so won't disrupt your existing legitimate users.
An important tool you can use to make this decision are App Check request metrics. You can monitor App Check metrics in the Google API Console or the Firebase Console.
Monitor Metrics in the Google API Console
To view metrics for your iOS OAuth client, navigate to the edit view of the client in the Credentials page. There, you will see metrics to the right of the page under the Google Identity for iOS section. These metrics will show you your App Check request metrics. The metrics include the following information:
- Number of verified requests - requests that have a valid App Check token. After you enable App Check enforcement, only requests in this category will succeed.
- Number of unverified requests: likely outdated client requests - requests missing an App Check token; these request may be from an older version of your app that doesn't include an App Check implementation.
- Number of unverified requests: unknown origin requests - requests missing an App Check token that don't look like they are coming from your app.
- Number of unverified requests: invalid requests - requests with an invalid App Check token, which may be from an inauthentic client attempting to impersonate your app, or from emulated environments.
Monitor Metrics in the Firebase Console
You can view metrics for your projects as a whole, or for individual OAuth clients:
To view the App Check request metrics for your project, open the App Check section of the Firebase console and expand the Google Identity for iOS section. For example:
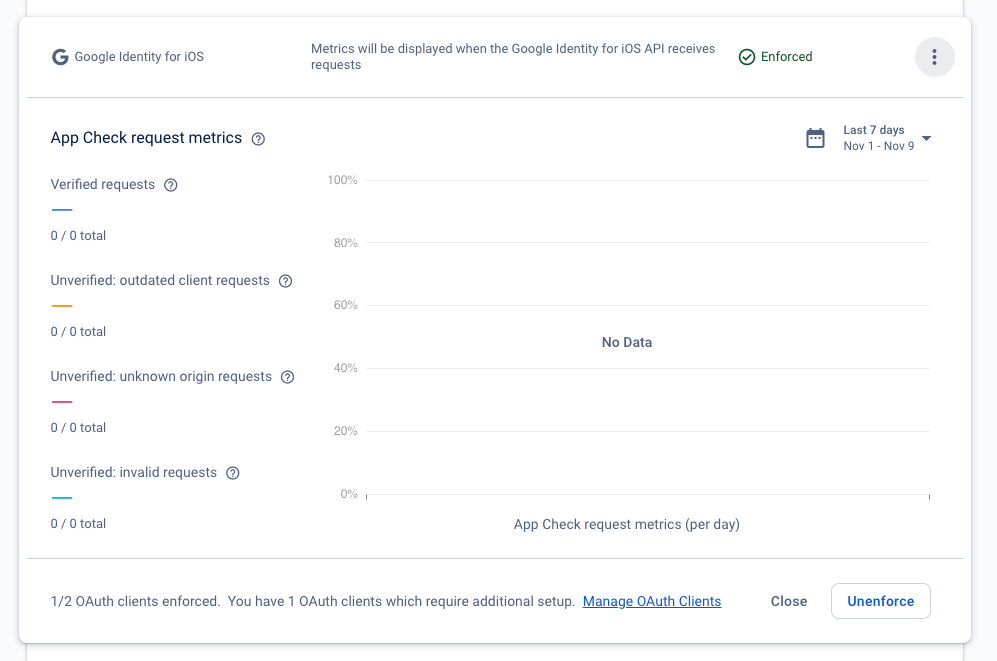
To view the App Check request metrics for a specific OAuth client, open the OAuth clients page of the Firebase console and expand the section corresponding to the client.
The request metrics are broken down into four categories:
Verified requests are those that have a valid App Check token. After you enable App Check enforcement, only requests in this category will succeed.
Outdated client requests are those that are missing an App Check token. These requests might be from an older version of the Firebase SDK before App Check was included in the app.
Unknown origin requests are those that are missing an App Check token, and don't look like they come from the Firebase SDK. These might be from requests made with stolen API keys or forged requests made without the Firebase SDK.
Invalid requests are those that have an invalid App Check token, which might be from an inauthentic client attempting to impersonate your app, or from emulated environments.
The distribution of these categories for your app should inform when you decide to enable enforcement. Here are some guidelines:
If almost all of the recent requests are from verified clients, consider enabling enforcement to start protecting your auth endpoints.
If a significant portion of the recent requests are from likely-outdated clients, to avoid disrupting users, consider waiting for more users to update your app before enabling enforcement. Enforcing App Check on a released app will break prior app versions that are not integrated with the App Check SDK.
If your app hasn't launched yet, you should enable App Check enforcement immediately, since there aren't any outdated clients in use.
Next steps
When you understand how App Check will affect your users and you're ready to proceed, you can enable App Check enforcement.